If you haven’t been using Azure Automation Accounts, they are a great way to script out nightly tasks in your environment and have them running as a Managed Identity (no users or passwords).
Your PowerShell scripts run within a Runbook which can be a collection of scripts that can be scheduled and ordered accordingly.
A few of the powerful features of Automation Accounts that I’ve been using/am interested in.
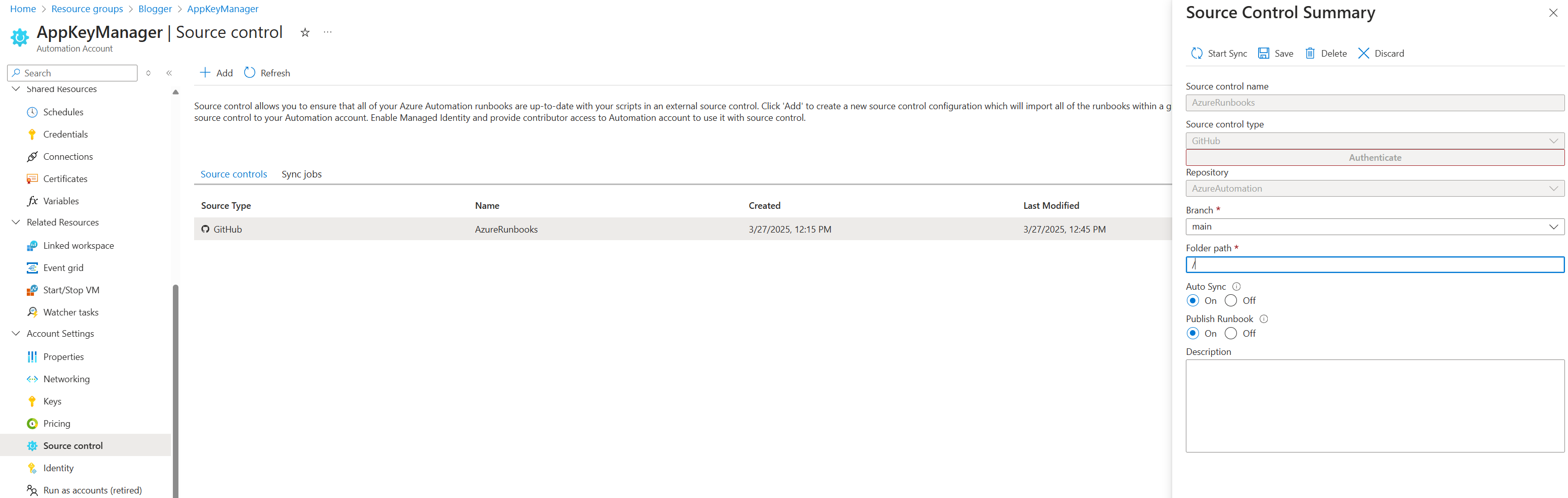
Source Control
You can connect your scripts to any GIT or Azure DevOps repository. This is great if your team is working remotely and you have people working on an editing script outside of the Azure Portal. Unfortunately, the syncing is only one way, from GIT to Azure, and not the other way
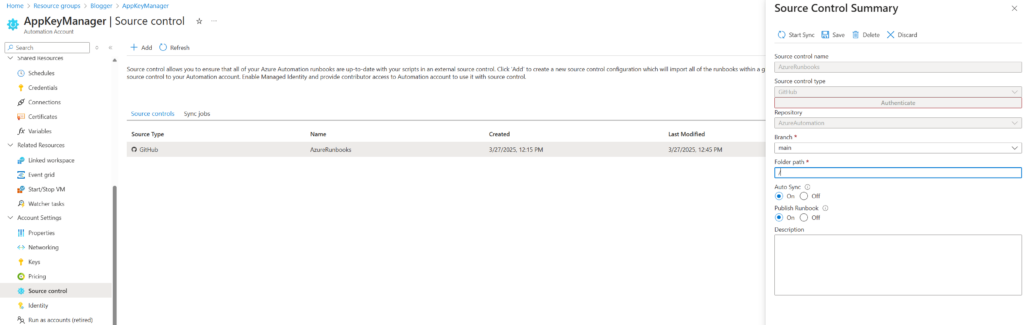
Variables
The use of variables is a great way not only to manage your variables and re-use them (so you don’t have them floating around all over the place) but also to ensure they are consistently used across your runbook.
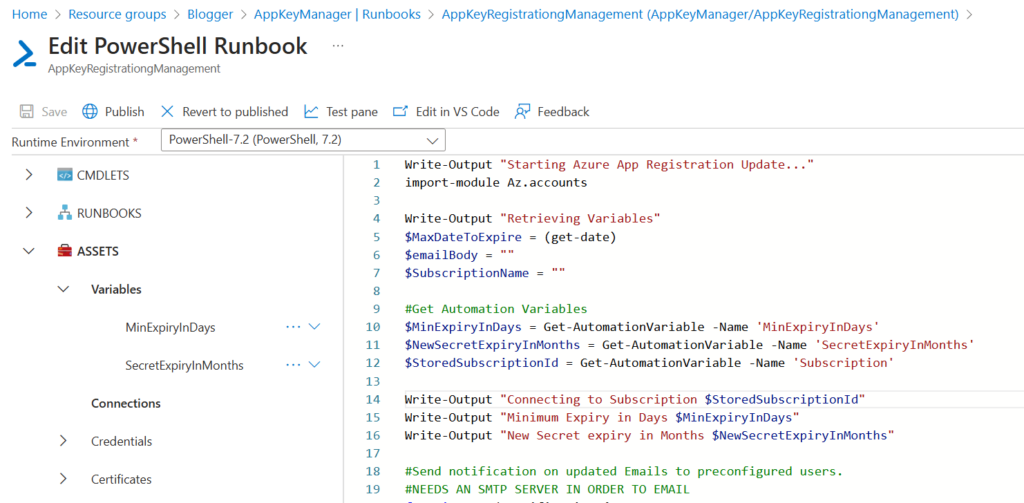
When declared at the runbook level, they can then be pulled into the powershell script as indicated below.
Azure Role Assignments
Although it can be painful figuring out the “secret sauce” of security roles to use. Going through the process ensures that you’re building a low-context automation service that doesn’t accidentally get granted lots of rights that are not needed.
Being able to grant rights at the Resource Group, Subscription, Key Vault, Storage or SQL level is a great way to reduce permissions.
Event Driven
I have not stepped into this yet, but I very much like the Event Grid support in Runbooks that would allow a runbook to trigger from a certain event (that’s on my next).
Lastly, there is an Azure Automation Extension for VSCode that I’ve been yearning to get into and that is next on my list.